Securing your edge
Chrome Enterprise Premium
Work no longer happens behind a castle wall. It happens in the browser. It’s time your security controls lived there, too.
For a long time, we secured the device and the network. This was simple (enough) because everyone worked in the same place. Today, whether you BYOD or WFH, your organisation’s data along with almost every high-value activity your staff undertakes, is accessed via the browser.
Traditional endpoint security can’t see what happens inside that session without the use of draconian tools and processes that hinder the momentum staff need to drive your business forward every day.
Chrome Enterprise Premium transforms the world’s most trusted browser into a centralised enforcement point for security, privacy and control – without getting in the way of success.
Your New Security Perimeter
Today, your staff are accessing data and tools far from the all-seeing eye of your IT administrator. They’re working from home, the coffee shop, on the train and on customer visits.
They mean well, so providing them access from anywhere seems reasonable. But, especially with the proliferation of new AI tools, you risk them accidentally pasting IP into public chatbots and other places that make it easier for threat actors to leverage.
Chrome Enterprise Premium brings your power back.
Preventing Data Loss
How do you stop an employee from pasting proprietary code into ChatGPT, or downloading a client list to a personal email account?
Protecting Against Threats
What are you doing to ensure that your organisation isn’t exposed to phishing attacks or malicious URLs, the entry point for 90% of cyberattacks?
Managing Temporary Access
How do you give contractors and temporary staff access to internal apps without the expense of provisioning and shipping a corporate device?
Granular Content Control
Preventing data exfiltration requires a more elegant solution than blanket-blocking USB ports when the real risk happens on-device in the browser.
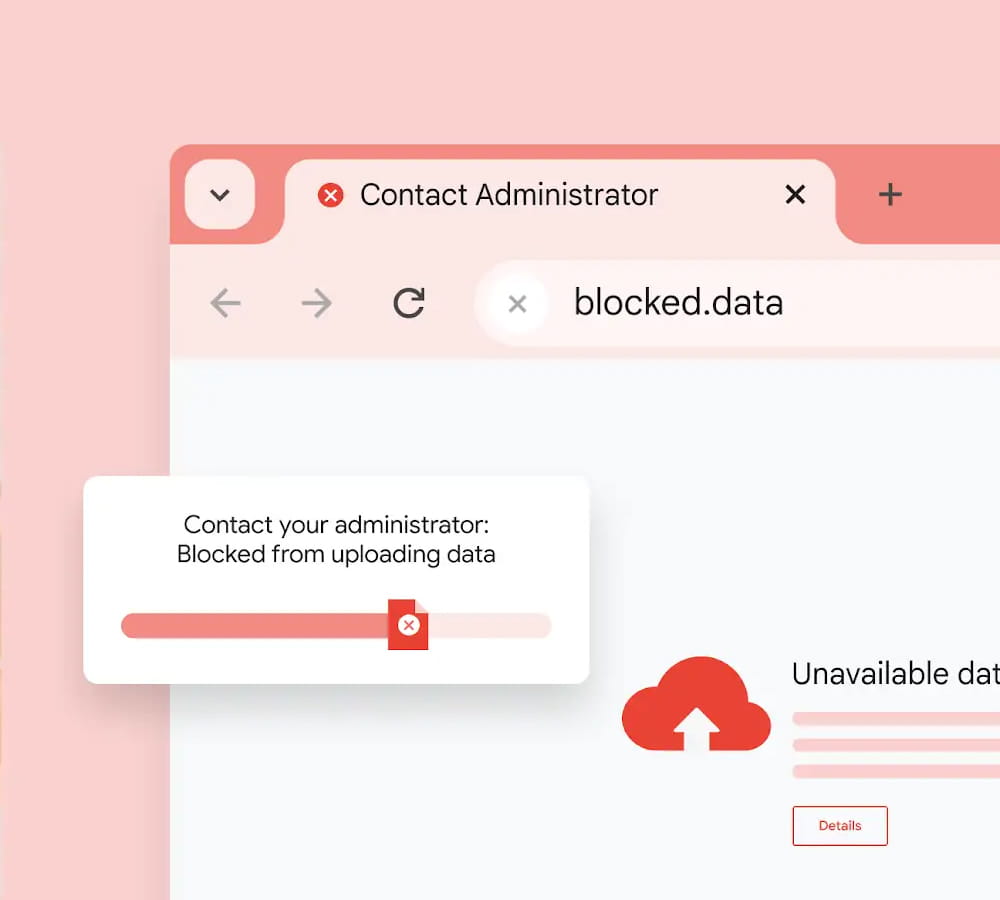
Chrome Enterprise Premium introduces powerful Data Loss Prevention (DLP) capabilities that enable IT teams to enforce policies by URL, category, or data type. You can prevent specific actions, like uploading files, printing sensitive documents or copy-pasting into unapproved AI chatbots.
For high-security environments, you can go even further by applying dynamic watermarking to sensitive pages, blocking screenshots entirely, or keep an Evidence Locker for forensic records of any file or data transfer that triggers your security rules.
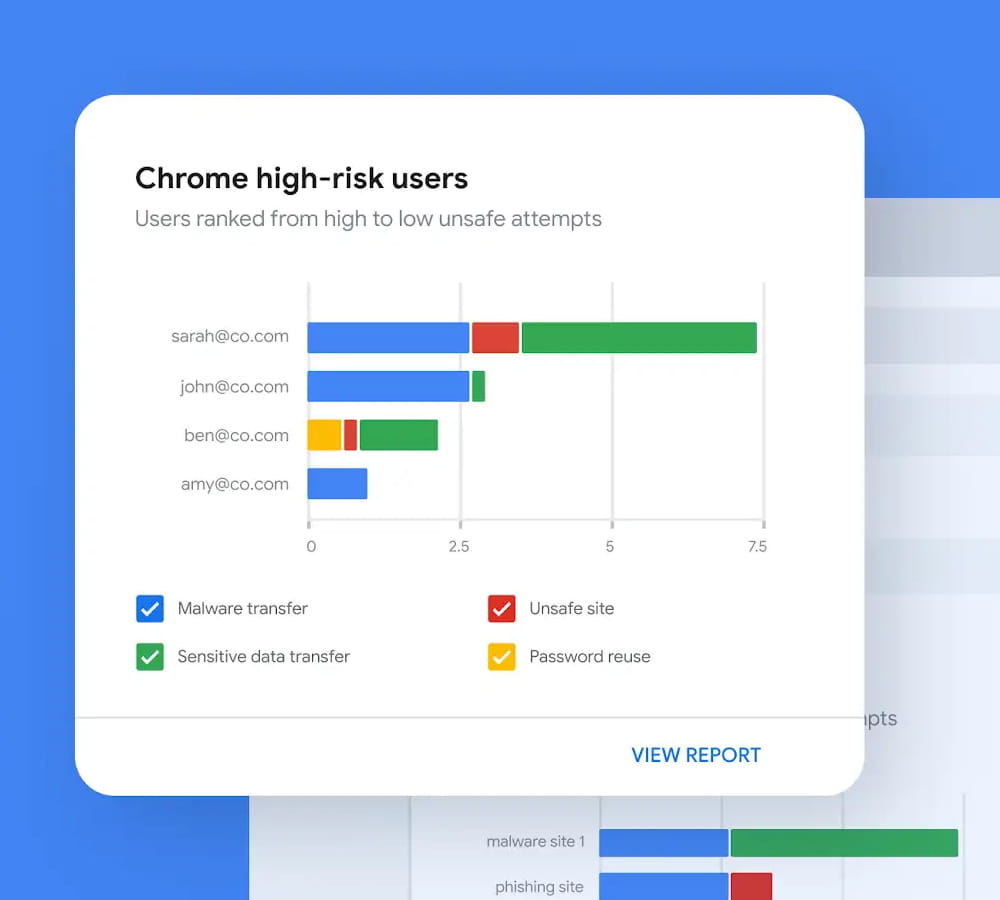
Google-Grade Threat Intelligence
Chrome Enterprise Premium moves your defence line beyond the traditional VPN by applying a Zero Trust model directly to the browser.
Leveraging Google’s world-class threat intelligence, it scans billions of URLs to provide real-time content analysis to block malware and phishing attempts before a malicious page can even render.
Crucially, this security isn’t limited to web apps. You can apply these same Zero Trust controls to non-web protocols like RDP, SCP and SSH to allow admins to manage infrastructure securely without the complexity of a VPN.
Secure the Profile, Not the Device
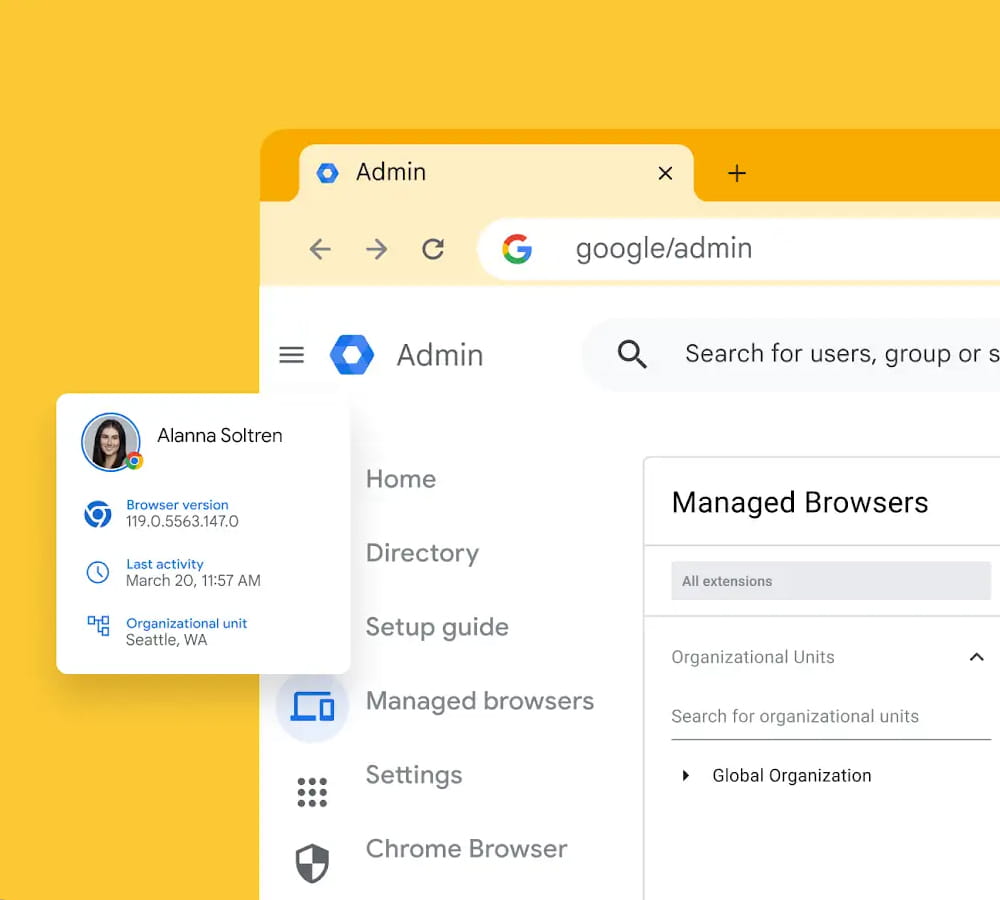
Chrome Enterprise Premium eliminates the trade-off between security and agility when managing an extended workforce of contractors and temporary staff by securing the browser profile rather than the physical device.
This means you can deploy advanced security capabilities instantly to any user, on any operating system. Contractors can simply sign in to a managed work profile on their personal device, allowing your corporate policies to be strictly enforced while their personal browsing remains private and untouched.
It is the fastest, most cost-effective way to onboard staff securely while respecting user privacy.
Comparing Key Capabilities
See the differences between Chrome Enterprise Core and Chrome Enterprise Premium.
| Capability | Chrome Enterprise Core | Chrome Enterprise Premium |
|---|---|---|
| Cost | Free Included |
Paid Licence |
| Management | Centralised Policy Management 300+ policies |
All Core features + Advanced Security |
| Visibility | Basic Reporting Version, OS, Extension usage |
Deep Security Insights & Data Protection Alerts |
| Data Protection | Basic Extension Management | Enterprise DLP Copy/Paste Block, Print Block, Watermarking |
| Threat Defence | Safe Browsing Standard |
Real-Time Malware & Phishing Analysis |
| Access Control | Basic Authentication | Context-Aware Access Zero Trust |
Partner with Getech
Our team of experts are ready to support you with each step of implementing your chosen solution, from procurement to deployment.
Ready to start a conversation?